Understanding Threatening Emails Demanding Bitcoin
Threatening emails demanding Bitcoin are a growing concern, leveraging fear and intimidation to extort money from victims. These emails often employ sophisticated tactics to appear credible and pressure recipients into complying with their demands. Understanding the characteristics of these emails is crucial for effective prevention and response.
These emails typically combine a sense of urgency with a credible-sounding threat to create a powerful psychological impact on the recipient. The threats themselves vary widely but generally aim to cause significant distress.
Threat Examples in Bitcoin Extortion Emails
The threats used in these emails are designed to instill fear and panic. Examples include threats of revealing personal information (like compromising photos or private details), damaging a computer system through malware, harming family members or pets, or even threats of physical violence. The specifics are tailored to what the scammer believes will be most effective for the individual victim. For instance, a threat to reveal compromising photos would be more effective against a victim who has such photos, while a threat to their computer system would be more effective against someone who is technologically vulnerable. The threat is always presented as imminent and unavoidable unless the Bitcoin ransom is paid.
Psychological Tactics Used in Bitcoin Extortion Emails
These emails employ several psychological tactics to pressure victims into paying. The most common include creating a sense of urgency (“You have 24 hours to comply”), exploiting fear of embarrassment or social repercussions (“We will share this information with your friends and family”), and leveraging the victim’s emotional vulnerability. The language is often aggressive and accusatory, designed to make the victim feel trapped and helpless. The perpetrators often play on the victim’s feelings of guilt, shame, or fear, making it difficult for them to think rationally and seek help. This emotional manipulation is a key element in their success rate.
Subject Lines Commonly Used in Bitcoin Extortion Emails
Subject lines are carefully crafted to pique the recipient’s interest and encourage them to open the email. They often use alarming or intriguing phrases to create a sense of urgency and importance. Examples include: “Urgent Security Alert,” “Your Private Data Has Been Compromised,” “We Have Your Password,” or more generic and less specific subject lines like “Important Information.” The goal is to avoid spam filters while also grabbing the victim’s attention.
Methods Used to Disguise Sender Identity and Location
Scammers employ various techniques to obscure their identity and location. They frequently use spoofed email addresses that appear to originate from legitimate organizations or individuals. They might also use anonymous email services or public Wi-Fi networks to mask their IP address and geographic location. Additionally, they might use translation services to obscure their native language, making it harder to trace their origin. The goal is to make it extremely difficult, if not impossible, to identify and prosecute them.
Responding to a Threatening Bitcoin Email: Threatening Email Asking For Bitcoin
Receiving a threatening email demanding Bitcoin is a serious situation requiring immediate and careful action. Ignoring the email is not an option; doing so could potentially embolden the perpetrator. Instead, a measured response focusing on preservation of evidence and reporting to the appropriate authorities is crucial. Remember, paying the ransom rarely guarantees the cessation of threats and often encourages further criminal activity.
Responding to such an email requires a calm and methodical approach. Panicking will only hinder your ability to effectively address the situation. The primary goal is to protect yourself, your data, and your finances while gathering evidence for law enforcement.
Steps to Take When Receiving a Threatening Email Demanding Bitcoin
The following actions should be taken immediately upon receiving a threatening email demanding Bitcoin. Prioritizing these steps will help mitigate potential harm and aid in the investigation.
- Do not respond to the email: Engaging with the sender, even to refuse their demands, can escalate the situation and provide them with more information. Any communication could be used against you.
- Preserve the email: Forward the email to a separate, secure email account or save it to an external hard drive. Do not delete it. This is crucial evidence for law enforcement.
- Take screenshots: Capture screenshots of the email, including headers, and any attached files. This provides additional evidence and preserves the original email’s integrity.
- Review your security: Change all your passwords, particularly those associated with financial accounts and online services mentioned in the email. Enable two-factor authentication wherever possible.
- Assess the threat: While you should not respond, evaluate the specificity of the threat. Is it a generalized threat, or does it contain specific details about you or your activities?
Reporting the Email to Relevant Authorities
Reporting the email to the appropriate authorities is a critical step in the process. This allows law enforcement to investigate the threat and potentially apprehend the perpetrator.
- Contact your local law enforcement: Report the incident to your local police department or the equivalent agency in your jurisdiction. Provide them with copies of the email and any screenshots you have taken.
- Report to the FBI’s Internet Crime Complaint Center (IC3): The IC3 is a centralized agency that receives reports of internet-related crimes, including email threats and extortion. Their website provides a detailed reporting form.
- Report to your email provider: Forward the email to your email provider’s abuse or security team. Many providers have specific procedures for handling phishing and threatening emails.
- Document the reporting process: Keep records of all reports filed, including dates, times, and case numbers. This will be helpful if you need to follow up on the investigation.
Preserving Evidence Related to the Email
Preserving all evidence related to the threatening email is paramount for a successful investigation. The information gathered can significantly aid law enforcement in identifying and prosecuting the perpetrator.
The importance of preserving digital evidence cannot be overstated. This includes the original email, screenshots, any attached files, and records of all communications related to the incident. Consider using forensic software if you have the technical expertise to create a secure and tamper-proof copy of the evidence.
Contacting Your Bank or Financial Institution
If the email threatens to compromise your financial accounts, contacting your bank or financial institution immediately is crucial.
Your bank or financial institution can assist you in monitoring your accounts for any unauthorized activity. They can also provide advice on protecting your financial information and help you secure your accounts. Report any suspicious activity to them immediately, providing them with details from the threatening email. They may be able to help freeze your accounts temporarily to prevent any fraudulent transactions.
Preventing Future Threatening Emails
Receiving threatening emails demanding Bitcoin or other cryptocurrency is a serious issue, but proactive measures can significantly reduce your risk. Implementing a multi-layered approach encompassing email security, strong passwords, and safe online practices is crucial for minimizing exposure to such threats. This involves both technical configurations and behavioral adjustments.
Protecting yourself from future threatening emails requires a proactive strategy involving both technical and behavioral changes. By strengthening your digital defenses and practicing safe online habits, you can drastically reduce the likelihood of becoming a target.
Email Filter and Spam Settings Configuration
Effective email filtering and spam settings are your first line of defense against unwanted emails, including threats. Most email providers offer robust tools to manage incoming messages. You should customize your spam filters to be more aggressive, marking emails from unknown senders as spam or deleting them outright. Consider adding specific s often found in phishing or threatening emails (e.g., “bitcoin,” “urgent payment,” “your account has been compromised”) to your filter’s blacklist. Regularly review your spam folder to ensure the filters are working effectively and adjust the settings as needed. Many providers also allow you to create rules that automatically delete emails from specific domains or containing particular phrases. Utilize these features to refine your email security.
Strong Passwords and Two-Factor Authentication
Strong passwords are fundamental to online security. Avoid easily guessable passwords, and instead use a combination of uppercase and lowercase letters, numbers, and symbols. Aim for passwords that are at least 12 characters long. Consider using a password manager to generate and securely store complex passwords for various accounts. Even stronger protection is offered by two-factor authentication (2FA), which adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone or email, in addition to your password. Enabling 2FA wherever possible, especially for your email account, significantly reduces the risk of unauthorized access, even if your password is compromised.
Best Practices for Online Safety and Security
Beyond technical settings, adopting safe online practices is vital. Be cautious about clicking links or downloading attachments from unknown senders. Legitimate organizations rarely communicate sensitive information via email. Regularly update your software and operating systems to patch security vulnerabilities. Avoid sharing personal information online unless absolutely necessary, and be wary of phishing scams designed to trick you into revealing sensitive data. Educate yourself about common online threats and scams to recognize and avoid them. Think before you click, and remember that if something seems too good to be true, it probably is. A healthy dose of skepticism can go a long way in protecting yourself from online threats.
Legal Ramifications and Law Enforcement
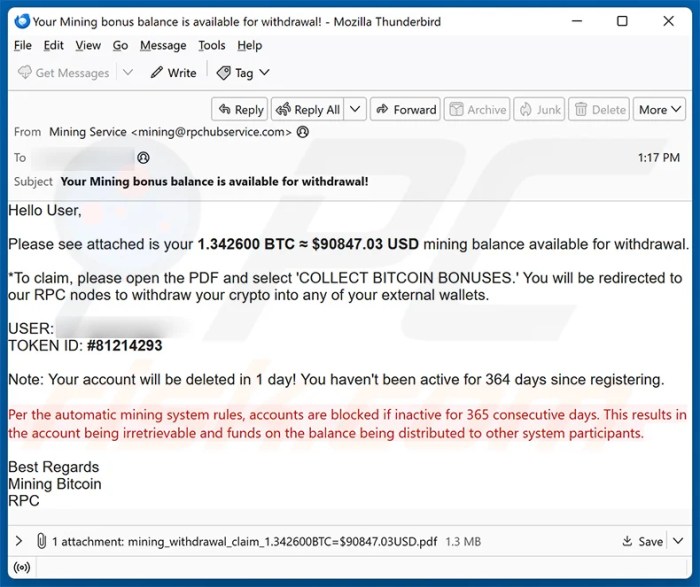
Sending threatening emails demanding Bitcoin carries significant legal consequences, varying depending on jurisdiction but generally falling under laws prohibiting extortion, cyberstalking, and threats of violence. These crimes can result in substantial fines and imprisonment. The severity of the punishment is influenced by factors such as the nature of the threat, the victim’s vulnerability, and the amount of Bitcoin demanded.
The legal ramifications extend beyond the sender; receiving and acting upon such threats, even if unknowingly facilitating the crime, can also have legal implications depending on the circumstances and jurisdiction. It’s crucial to understand that ignorance of the law is not a defense.
Consequences for Sending Threatening Emails Demanding Bitcoin
Sending threatening emails demanding Bitcoin is a serious crime with severe penalties. Depending on the jurisdiction and specific details of the case, charges could include extortion, cyberstalking, harassment, and even terrorism-related offenses if the threat involves significant harm or targets critical infrastructure. Sentences can range from substantial fines to lengthy prison terms. For instance, in the US, the penalties under the Computer Fraud and Abuse Act (CFAA) and various state laws can be particularly severe. In the UK, the Computer Misuse Act 1990 and other relevant legislation provide for prosecution and punishment for such cybercrimes. International cooperation plays a vital role in prosecuting offenders, particularly in cases involving cross-border transactions.
Resources Available to Victims of Cybercrime
Victims of cybercrime, including those targeted by threatening emails demanding Bitcoin, have access to various resources. Many countries have dedicated cybercrime units within their law enforcement agencies. Furthermore, numerous organizations provide support and guidance to victims, offering assistance with reporting the crime, recovering lost funds (where possible), and providing emotional support. These organizations often offer advice on securing online accounts and preventing future incidents. Examples include the Internet Crime Complaint Center (IC3) in the United States and Action Fraud in the United Kingdom. These resources can provide critical assistance in navigating the legal and emotional challenges faced by victims.
Law Enforcement Handling of Threatening Bitcoin Email Cases
Law enforcement agencies approach these cases by tracing the origin of the emails, identifying the sender through IP addresses and other digital footprints, and collaborating with financial institutions to track Bitcoin transactions. International cooperation is often crucial as Bitcoin transactions can cross borders quickly. Investigations often involve sophisticated forensic techniques to analyze digital evidence and build a strong case for prosecution. The complexity of these investigations depends on the sophistication of the perpetrators and the availability of evidence. Successful prosecutions often rely on the cooperation of victims in providing information and preserving evidence.
International Cooperation in Investigating Cybercrimes, Threatening Email Asking For Bitcoin
International cooperation is vital in investigating cybercrimes involving Bitcoin, as criminals often operate across borders. Law enforcement agencies rely on international treaties, agreements, and mutual legal assistance treaties (MLATs) to share information, conduct joint investigations, and extradite suspects. Interpol plays a significant role in facilitating international cooperation by providing a platform for communication and coordination among law enforcement agencies worldwide. Effective international cooperation is essential for successfully prosecuting offenders and deterring future cybercrimes. The complexity of tracing Bitcoin transactions across multiple jurisdictions highlights the importance of these international collaborations.
The Psychology Behind Bitcoin Extortion
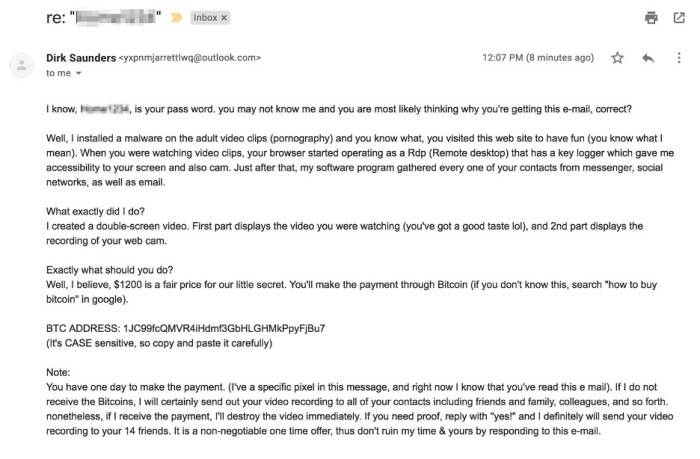
Bitcoin extortion leverages a potent combination of technological anonymity and psychological manipulation to coerce victims into paying ransoms. The perpetrators often target individuals or organizations perceived as vulnerable or possessing valuable data, aiming to maximize their financial gain while minimizing their risk of apprehension. Understanding the motivations behind these attacks is crucial in developing effective prevention and response strategies.
The allure of Bitcoin for extortionists stems primarily from its perceived anonymity. Unlike traditional financial systems, Bitcoin transactions are pseudonymous, meaning they are not directly tied to the user’s real-world identity. This characteristic makes it difficult for law enforcement to trace the flow of funds, creating a sense of impunity for the perpetrators. The decentralized nature of the Bitcoin network further complicates investigations, as there is no central authority to request transaction details or freeze accounts. However, it’s crucial to remember that complete anonymity is an illusion; sophisticated investigative techniques can still uncover the identities of Bitcoin users involved in illicit activities.
Bitcoin’s Anonymity and its Role in Cybercrime
Bitcoin’s pseudonymous nature, while not providing absolute anonymity, significantly lowers the barrier to entry for cybercriminals. The relative ease of creating Bitcoin wallets and the lack of stringent Know Your Customer (KYC) regulations compared to traditional banking systems make it an attractive tool for illicit activities. The decentralized and borderless nature of the cryptocurrency further enhances its appeal to those seeking to operate outside the reach of traditional law enforcement. While blockchain technology provides a transparent record of transactions, linking these transactions to specific individuals requires investigative expertise and often cooperation between law enforcement agencies across different jurisdictions.
Comparison of Bitcoin Extortion with Other Online Threats
Bitcoin extortion shares similarities with other forms of online threats, such as ransomware and phishing, but also presents unique challenges. Like ransomware, Bitcoin extortion involves demanding payment for the release of stolen or compromised data. However, unlike ransomware, which typically encrypts a victim’s data, Bitcoin extortion often involves threats of data exposure or other forms of reputational damage. Phishing attacks can be used to obtain Bitcoin wallet information or to trick victims into transferring funds directly. The key difference lies in the payment method: Bitcoin’s pseudonymous nature distinguishes it from traditional extortion schemes that rely on traceable payment methods.
Vulnerabilities Exploited in Bitcoin Extortion Attacks
Bitcoin extortion attacks frequently exploit vulnerabilities in an organization’s security posture or individual’s personal habits. These vulnerabilities can range from weak passwords and outdated software to social engineering tactics that exploit human psychology. For example, a phishing email might leverage a sense of urgency or fear to convince a victim to transfer Bitcoin. Similarly, a threat to release sensitive data, such as personal information or business secrets, can be highly effective in coercing payment. The perceived anonymity of Bitcoin enhances the effectiveness of these attacks by making tracing and prosecution significantly more difficult. Furthermore, the lack of readily available and user-friendly tools for tracking and recovering lost Bitcoin contributes to the success rate of these schemes.
Frequently Asked Questions (FAQ)
Receiving a threatening email demanding Bitcoin can be a frightening experience. This section addresses common concerns and provides practical guidance on how to respond and protect yourself. Understanding your options and the legal landscape is crucial in navigating this situation effectively.
Actions to Take Upon Receiving a Threatening Bitcoin Email
Upon receiving such an email, immediately cease all communication with the sender. Do not engage, respond, or attempt to negotiate. Report the email to your internet service provider (ISP) and the relevant law enforcement agencies. Preserve all evidence, including the email itself, any attachments, and any communication you may have inadvertently sent. Consider contacting a cybersecurity professional for assistance in assessing potential vulnerabilities and ensuring the security of your systems.
Bitcoin Transaction Traceability
While Bitcoin transactions are pseudonymous, meaning they don’t directly reveal the sender’s or recipient’s identity, they are not entirely untraceable. Law enforcement agencies utilize blockchain analysis techniques and collaborate with cryptocurrency exchanges to track transactions. The success of tracing depends on factors such as the sophistication of the attacker’s techniques to obscure their identity and the resources available to investigators. A significant transaction or a pattern of suspicious activity is more likely to be traced.
Law Enforcement’s Ability to Recover Stolen Bitcoin
The chances of law enforcement recovering stolen Bitcoin vary significantly depending on several factors. These include the speed of reporting, the complexity of the attacker’s methods, the jurisdiction involved, and the resources dedicated to the investigation. In some cases, law enforcement has successfully seized Bitcoin and returned it to victims, particularly when the perpetrators made mistakes or used identifiable exchanges. However, there is no guarantee of recovery, and the process can be lengthy and complex.
Protecting Against Future Threats
Proactive measures are essential to mitigate the risk of future threats. Strong passwords, multi-factor authentication (MFA) for all online accounts, and regular software updates are fundamental. Being cautious about phishing emails and suspicious links is crucial. Educating yourself about common online scams and staying informed about evolving threats can significantly improve your security posture. Consider using reputable anti-virus and anti-malware software.
Legal Recourse for Victims of Bitcoin Extortion
Victims of Bitcoin extortion have several legal avenues they can explore. Reporting the crime to law enforcement is the first step. They can also seek legal counsel to explore civil remedies, potentially suing the perpetrator for damages. The success of legal action depends on the evidence available and the jurisdiction’s laws regarding cybercrime. It’s crucial to consult with a lawyer specializing in cybercrime and digital asset recovery to understand your options and the likelihood of a successful outcome.
Illustrative Examples (using HTML table)
Understanding the characteristics of threatening Bitcoin emails is crucial for effective response and prevention. The following examples illustrate common tactics used by extortionists, highlighting key red flags to watch out for. Careful examination of these examples will improve your ability to identify and respond appropriately to such threats.
| Subject Line | Email Excerpt | Red Flags | Explanation of Red Flags |
|---|---|---|---|
| URGENT: Your Data Has Been Compromised | “We have full access to your computer and have been monitoring your activities for some time. We have compromising information about you that we can release publicly unless you pay us 1 Bitcoin within 24 hours.” | Generic Threat, Time Sensitivity, Demand for Bitcoin | Generic threats lack specific details, making them less credible. The tight deadline creates pressure to act rashly. Bitcoin’s untraceability is a common tactic for anonymity. |
| Your Account Has Been Hacked | “We have gained access to your email account and social media profiles. We can share embarrassing photos and videos with your contacts unless you send us 0.5 Bitcoin within 48 hours.” | Vague Claims, Threat of Social Damage, Implied Possession of Data | The email lacks specific evidence of account compromise. The threat focuses on reputational damage, a common tactic. The implication of possessing data, without providing proof, is a major red flag. |
| Payment Required Immediately | “You have 72 hours to send 1.2 Bitcoin to the address below. Failure to comply will result in serious consequences. We know where you live.” | Implied Violence, Unclear Consequences, Direct Bitcoin Demand | The threat of “serious consequences” is vague and meant to instill fear. The lack of specifics about the consequences is a tactic to maximize intimidation. The direct demand for Bitcoin shows the extortionist’s intent. |
| Security Breach Notification | “Your online banking details have been compromised. We can transfer funds from your account unless you send 0.8 Bitcoin to the specified address. Act now to prevent further loss.” | Financial Threat, Urgency, Specific Payment Demand | The threat targets financial security, a highly sensitive area. The urgency is designed to bypass rational thought. The precise amount of Bitcoin requested is a common tactic. |
Table Explanation
The table above provides four examples of threatening emails demanding Bitcoin. Each example highlights key characteristics often found in these types of extortion attempts. Analyzing these examples allows for better identification of similar threats in the future. Note that the specific details may vary, but the underlying tactics remain consistent.
Safe Practices for Online Communication
Protecting yourself from malicious emails and online threats requires a proactive approach to online communication. By implementing robust security measures and practicing safe online habits, you significantly reduce your vulnerability to extortion attempts and other cybercrimes. This section details key practices to minimize your risk.
Threatening Email Asking For Bitcoin – Safe online communication involves a multi-faceted approach encompassing email etiquette, responsible social media engagement, and strong password management. Negligence in any of these areas can increase your susceptibility to phishing scams and other forms of online exploitation, leading to potentially devastating consequences.
Email Security Practices
Email remains a primary vector for malicious attacks. Therefore, adopting secure email practices is crucial in mitigating the risk of receiving threatening emails.
- Avoid opening emails from unknown senders: Delete suspicious emails immediately without opening them. Never click on links or attachments from unverified sources.
- Enable two-factor authentication (2FA): This adds an extra layer of security to your email account, making it significantly harder for unauthorized individuals to access your inbox.
- Use strong and unique passwords: Avoid using easily guessable passwords. Employ a password manager to generate and store complex, unique passwords for all your online accounts.
- Regularly review your email settings: Check your email account settings periodically to ensure that security features are enabled and that you are not inadvertently sharing personal information.
- Report phishing emails: Forward suspicious emails to your email provider’s abuse or phishing reporting address. This helps them identify and remove malicious content from their systems.
Social Media Safety
Social media platforms, while valuable for communication, can also expose you to online threats. Careful management of your online presence minimizes your vulnerability.
- Limit personal information shared online: Avoid posting sensitive details such as your home address, phone number, or financial information on social media.
- Review your privacy settings: Regularly review and adjust your privacy settings on all social media platforms to control who can see your posts and information.
- Be cautious about friend requests: Only accept friend requests from people you know and trust. Be wary of requests from strangers.
- Think before you post: Consider the potential consequences before sharing anything online. Remember that once something is posted online, it can be difficult to remove completely.
- Report suspicious activity: Report any suspicious activity or harassment on social media platforms to their respective support teams.
Password Management Best Practices
Strong and unique passwords are the cornerstone of online security. Poor password practices significantly increase the likelihood of account compromise, potentially leading to email threats.
- Use a password manager: Password managers generate strong, unique passwords for each account and securely store them, eliminating the need to remember numerous complex passwords.
- Avoid reusing passwords: Never reuse the same password across multiple accounts. If one account is compromised, attackers could gain access to others using the same password.
- Enable multi-factor authentication (MFA): Wherever possible, enable MFA for all your online accounts. This adds an extra layer of security beyond just a password.
- Regularly update passwords: Change your passwords regularly, especially for critical accounts such as email and banking.
- Choose strong passwords: Use a combination of uppercase and lowercase letters, numbers, and symbols to create strong, difficult-to-guess passwords.
Receiving a threatening email demanding Bitcoin is unfortunately becoming more common. Understanding the cryptocurrency’s mechanics can help contextualize these threats; for instance, learning about the process of acquiring Bitcoin, such as through mining, which you can explore further by reading about What Is Bitcoin Mining , is crucial. This knowledge can help you assess the feasibility of the demands and perhaps even aid in reporting the incident to the appropriate authorities.
Receiving a threatening email demanding Bitcoin is unfortunately becoming more common. The rising value of the cryptocurrency, as seen in recent reports on the Bitcoin All Time High , likely fuels these attacks. Criminals see Bitcoin’s high value and relative anonymity as an attractive payment method, making it crucial to report such incidents to the appropriate authorities and avoid engaging with the sender.
Receiving a threatening email demanding Bitcoin is unsettling, to say the least. Understanding the mechanics of cryptocurrency might seem daunting, but it’s crucial for navigating such situations. If you need to learn how to acquire Bitcoin, perhaps to understand the context of the threat, you can find a helpful guide on How To Buy Bitcoins. Remember, never engage with or comply with demands from threatening emails; instead, report it to the appropriate authorities.
Receiving a threatening email demanding Bitcoin is unfortunately becoming more common. The urgency often stems from the perceived value of the cryptocurrency, prompting immediate action from the victim. To understand the potential financial impact of such a demand, it’s helpful to check the current value; you can see the latest conversion rate by looking up 1 Bitcoin To Usd.
Knowing this exchange rate helps to assess the seriousness of the threat and potentially inform law enforcement investigations into these extortion attempts.
Receiving a threatening email demanding Bitcoin is unfortunately becoming more common. Understanding the current value is crucial in assessing the threat; checking the Bitcoin price today is a good first step, which you can easily do by visiting Precio Del Bitcoin Hoy. This helps determine the potential financial impact and guides your response to such a serious situation.
Remember, never engage with these types of threats directly.
